 WASHINGTON: As satellite operators scramble to join the 5G revolution, there is growing concern that weakness in US regulatory standards for cybersecurity could mean commercial networks could be full of holes for hackers to exploit.
WASHINGTON: As satellite operators scramble to join the 5G revolution, there is growing concern that weakness in US regulatory standards for cybersecurity could mean commercial networks could be full of holes for hackers to exploit.
DoD currently requires that all satellite operators who sign contracts encrypt their data links to ground stations using NSA-approved methods.
But as the US military looks for increased bandwidth to support its vision for a 5G-wired force to underpin global All-Domain Operations, it may find itself faced with having to rely — at least in the near-term — on providers of space-based Internet connectivity who are not practicing good cyber hygiene.
“Many satellites run on Linux and communicate over commonly hacked channels, including VHF, UHF and S-band. Some satellite communications transmissions are encrypted, some are not. This lack of security is leaving the door wide open for potential satellite attack. We’re developing this perfect storm of IoT devices in space with little thought for security and potentially disastrous consequences,” Ray Petty vice president of software firm Wind River Systems, said.
(He speaks from some experience, as Wind River last year suffered a major embarrassment when one of their most-used operating systems, VxWorks, was discovered to have 11 major flaws that could allow a hacker to take over the devices — including satellite modems.)
This is in part because regulations governing commercial sat operators issued by the Commerce Department and the Federal Communications Commission (FCC) lack specific requirements for cybersecurity, including for encrypting satellite uplinks and telemetry.
“There are few mandated security standards must be met before a satellite is launched,” Petty told a webinar yesterday sponsored by Viasat.
Indeed, a number of government and industry experts were bemused by new regulations on remote sensing satellites issued by the Commerce Department in May, which stopped short of ordering satellite operators to encrypt their data streams. The Commerce decision followed the the similar tack taken by the FCC in its revised debris mitigation rules for commercial satcom operators issued in April.
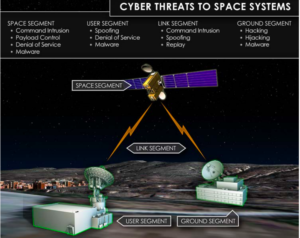
Cyber threats to space systems, NASIC 2018
“The U.S. missed a chance to lead by extending existing de facto requirements for commercial national security space providers to apply more broadly to key satellite subsystems,” Andrew D’Uva, president of Providence Access Company and US industry chair of the Space Force/National Security Agency’s Commercial Space INFOSEC Working Group (CSIWG), told me in an email today.
“The FCC and Commerce should require prospective satellite operators to demonstrate that they can maintain positive control of their maneuverable satellites and communications payloads against known threats before authorizing them,” he said.
Because the regulators don’t have set requirements, said one expert, some satellite operators simply are choosing to “roll their own” cybersecurity practices — in an obvious jab at SpaceX founder Elon Musk, who infamously was captured on a podcast smoking a joint (a stunt that led to a NASA review of the firm.)
SpaceX, with its Starlink program, is building a mega-constellations of thousands of small satellites to create a space-based Internet of Things (IoT). SpaceX didn’t respond to a request for comment about its cybersecurity practices by press time.
SpaceX is not alone in seeking to take the Internet to space. Amazon is another US corporate giant planning a mega-constellation for IoT connectivity — in part to power its own planned future fleet of delivery drones. And a number of companies outside the US are planning similar on-orbit broadband constellations.
More Satellites, More Cybersecurity Holes?
So, the rush to 5G could exacerbate current satellite vulnerabilities simply as the number of satellites soars, several experts said.
“One of the things that is unique about some of these newer operators is the number of spacecraft that we’re operating is increased fairly substantially over what you may have done from a legacy perspective. … [T]here are many more targets to try to go after,” William Eshagh, VP of Information Technology at remote sensing startup Planet, told a separate webinar today held as part of the annual CyberSat conference being held digitally this year, due to the coronavirus pandemic.

NASIC image
Other experts advised against making sweeping generalizations about the vulnerability of satellites carrying 5G traffic, versus that of terrestrial networks using fiber optics and cell towers.
“Don’t drink the Kool-Aid that all satellites are insecure,” one satellite cybersecurity expert told me yesterday. “It depends. And it’s complicated.”
“For the most part, the satellites, ground stations, end-user equipment, and links in operation today were designed, built, deployed when cyber vulnerabilities were not fully appreciated. I believe future space systems will have cyber protection built in, but that does not mean they will be immune from cyber vulnerabilities we don’t yet understand or appreciate. This is the case with 5G—when it comes online worldwide it will present new opportunities and challenges, and commercial, civil, and military space organizations will need to remain vigilant.” Chris Bogdan, vice chairman of the board, at Space ISAC, said in an email today. The Space ISAC is an industry-government group dedicated to cybersecurity of space assets.
“Securing satellite command uplinks and telemetry from effective remote attacks is routinely accomplished using proven cryptographic space and ground solutions by operators who seek to provide service to the Department of Defense, and has long been required by policy as an integral part of DoD’s acquisition strategy for commercial satellite communications services,” D’Uva said. “These NSA-approved commercial solutions can be employed on all but the smallest satellites, though some recent operators have elected not to adopt them.”
Lack of Coherent 5G Security Rules
Rather than satellites or wireless networks providing connectivity, several experts explained, the central cybersecurity issues revolve around the devices that are connected to the Internet. 5G is important to making IoT real because it vastly improves on current 4G telecommunications capabilities. It will increase speed, shorten latency (the lag-time in communications), and expand connectivity to the Internet and to each other for myriad electronic devices — from autonomous cars to smart fridges to a soldier’s backpack radio.
“The deployment of 5G capabilities will also be far more disruptive than those of prior generations, with transformative effects that extend well beyond telecommunications,” Petty said. “5G networks will enable vastly more smart devices to connect to the Internet, thereby accelerating the digital transformation that’s already underway in aerospace and defense, manufacturing, transportation, healthcare and government.”
As Breaking D readers know, DoD Research and Engineering czar Mike Griffin has made accelerating 5G network deployment his Nr. 2 goal. DoD is rushing to launch experiments in 5G connectivity at numerous bases. Further, the Trump administration has made outpacing China in the race to 5G a top priority; with administration officials waging a global campaign to thwart China’s telecommunications giant Huawei from dominating the market in 5G related technology — alleging that it is being used by the Chinese government to commit cyber espionage.
But just like with satellites, putting together cybersecurity solutions for 5G communications networks is being hampered by the absence of standardized technological protocols, as well as shifting government policies. As Sydney reported last November, a report by the Center for New American Security found that the US government needs to do more to ensure that the 5G networks used in the US and by allied and partner nations are secure if it wants to truly compete with China on the global marketplace.
“The transition to 5G is challenged by key standards, security principles and spectrum policies that are still in development,” Petty said. “Other related factors impacting the cost and speed of this deployment include industrial policy, fair market access, and government incentives.”
Slow DoD Progress
That said, Petty noted that DoD is making some progress with cybersecurity by moving to require the use of DevSecOps for software development, a process that requires security measures to be “baked in” upfront. This push is being led by the Air Force, he said. As Breaking D readers know, Air Force acquisition czar Will Roper has been a champion of DevSecOps.
Among other remediation measures he recommended, Petty opined that the two best technical standards available today for ensuring cybersecurity in satellite systems are the National Institute of Standard and Technology’s NIST-SP 800-171, which was just updated in February, and the Aerospace Industries Association’s NAS9933.
D’Uva noted that while the roughly 170 controls from the NIST standard are helpful, they are focused on protecting confidentiality of information and do not emphasize the two other security objectives for telecommunications networks: integrity and availability.
He explained that Space Force’s Commercial Satellite Communications Office (CSCO) “recently released details on its IA-PRE program, which will use third-party assessors to document how commercial SATCOM service providers apply more than 475 controls and enhancements drawn from NIST SP 800-53 to their systems”
The program, D’Uva said, will “assign a system risk rating” to create a list of approved products.
“The Space Force CSCO is leading here, but industry needs to commit to meeting the security requirements. Some are, and some won’t,” D’Uva said. “The government needs to value and pay for effective solutions, reject insecure offerings, and send a clear signal to the market that cybersecurity is critical. Our nation shouldn’t rely on providers who take shortcuts or ignore security in their development and operations. As we grown more dependent on network capabilities we need to up our game.”
Major trends and takeaways from the Defense Department’s Unfunded Priority Lists
Mark Cancian and Chris Park of CSIS break down what is in this year’s unfunded priority lists and what they say about the state of the US military.


























