SOURCE: Cyberspace Solarium Commission
WASHINGTON: “Our adversaries feel no fear,” Sen. Angus King said today, and that needs to change. Russian and Chinese leaders have grown accustomed to attacking the US in cyberspace with impunity, he said, and the government needs to make it clear to them that America will strike back: “If you attack us,” he said, “you will pay a price.”
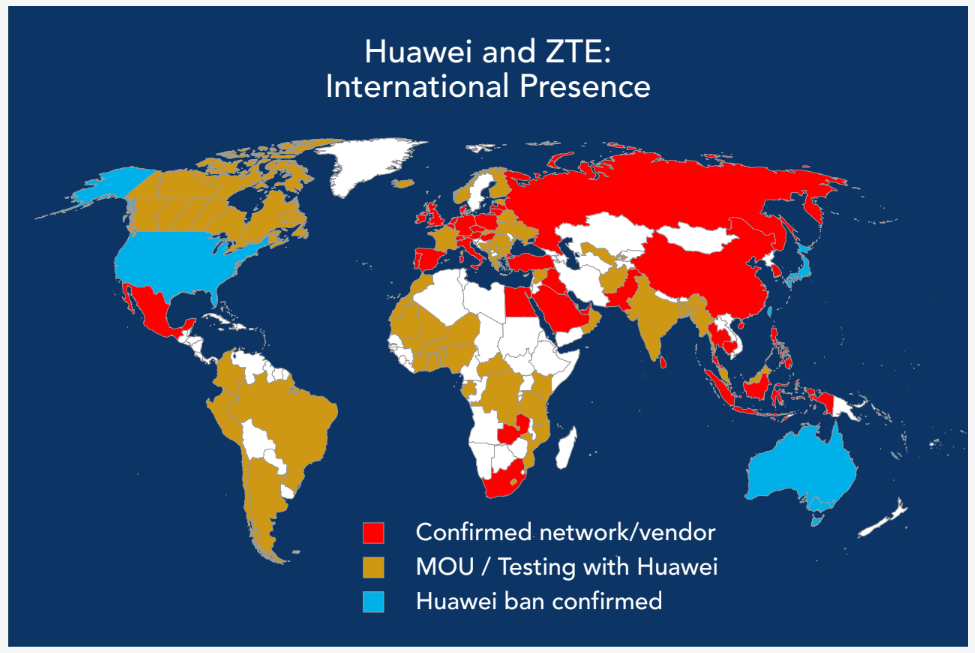
King was rolling out the final report of the Cyberspace Solarium Commission chartered by Congress, chaired by himself and Rep. Mike Gallagher – a report which deliberately and repeatedly invokes the analogy of Cold War deterrence. King even took pains to publicly praise President Trump’s hardline stance against Chinese 5G giant Huawei, which the report calls out as a threat.

Sen. Angus King
Now, much of both the 182-page report, released this morning, and the panel discussions held on Capitol Hill this afternoon focused on the usual suspects rounded up by any blue-ribbon commission. The report calls for reform and reorganization in both the Executive Branch and Congress, where oversight of cybersecurity is scattered among 50-plus committees. It calls for restoring and strengthening the White House cyber coordinator role abolished under Trump – a recommendation where the Republican Rep. Gallagher is publicly bucking his president — and for creating a new assistant secretary of State. It calls for government and business to work more closely together, sharing information on threats without imposing new regulation. It calls for closer cooperation with allies and the strengthening of international norms against bad actors. All these recommendations are as unsurprising as they are difficult to actually carry out.
But running through the usual high-minded mush was a remarkably hard line of realpolitik about the importance of retaliation. The soft-spoken King, one of the Senate’s most affable figures, actually raised the topic not quite nine minutes into the opening ceremonies.
“I’ve sat through probably 25 or 30 hearings before joining this commission,” King said. “One of the things that comes through is our adversaries feel no fear of costs being imposed.
“If the Russians can meddle with an election and have no serious consequences, why wouldn’t they do it again? If the Chinese can steal the OPM (Office of Personnel Management) records with more or less impunity, why wouldn’t they do it again?” King asked. “So part of the important function of the report is to talk about deterrence, and to talk about a declaratory policy that, if you attack us, you will pay a price. Because I want the people making these decisions, whether it’s in the Politburo or in the Great Hall of the People or whoever it is, to say, ‘man, if we do this, it’s going to cost us something.’”
Even King’s Freudian slip is telling: The Politburo – aka the Presidum, aka the Political Bureau of the Central Committee of the Communist Party of the Soviet Union – went out of existence with the USSR in 1991. (China’s Great Hall of the People, a building just by Tiananmen Square, remains in use). But the Politburo was the core decision-making body for America’s great rival for over 40 years. The Cyberspace Solarium Commission itself was named after President Eisenhower’s White House strategy sessions that roughed out the policy of containment. It’s that Cold War thinking that King & co. are deliberately seeking to revive.
Retaliation in Black & White
Like King’s remarks today, the text of the report itself moves swiftly to deterrence and retaliation.
“Here are some big ideas to get the conversation started,” King and Gallagher write in their introduction. “First, deterrence is possible in cyberspace. Today most cyber actors feel undeterred, if not emboldened, to target our personal data and public infrastructure. In other words, through our inability or unwillingness to identify and punish our cyber adversaries, we are signaling that interfering in American elections or stealing billions in U.S. intellectual property is acceptable. The federal government and the private sector must defend themselves and strike back….”
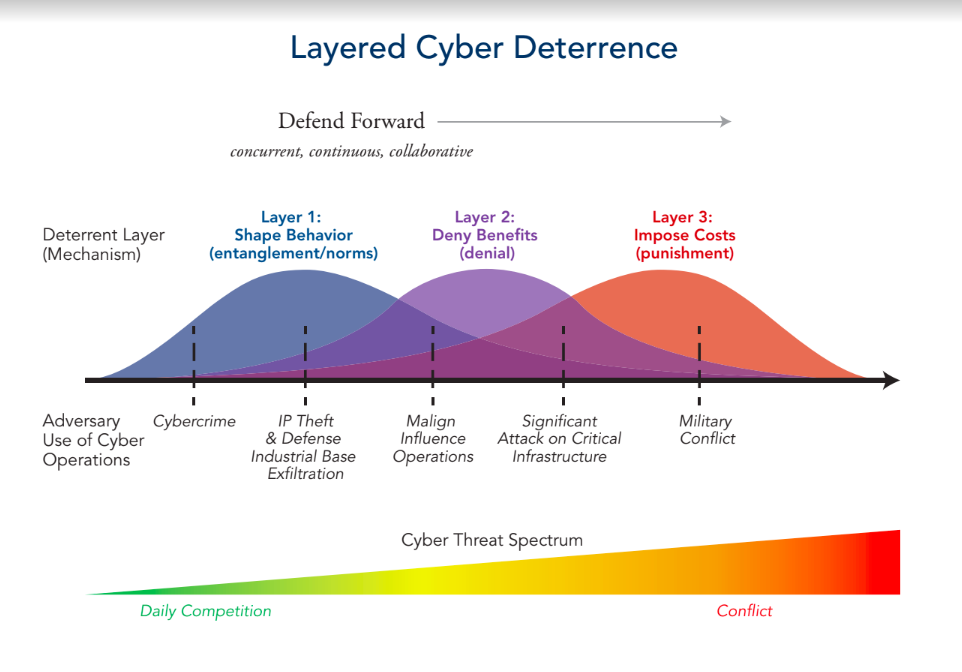
The body of the report calls for a strategy of “layered deterrence,” with three mutually supporting layers. They are:
- Shape behavior. The United States must work with allies and partners to promote responsible behavior in cyberspace.
- Deny benefits. The United States must deny benefits to adversaries who have long exploited cyberspace to their advantage, to American disadvantage, and at little cost to themselves. This new approach requires securing critical networks in collaboration with the private sector to promote national resilience and increase the security of the cyber ecosystem.
- Impose costs. The United States must maintain the capability, capacity, and credibility needed to retaliate against actors who target America in and through cyberspace.
The Cold War language of deterrence run through the report. Yes, the report does distinguish – like Cold War theorists – between “deterrence by denial,” which means defending yourself so well that potential attackers doubt they’ll do the damage they desire, and “deterrence by punishment,” which means being able to stage a counter-offensive so devastating that would-be attackers lose more than they could hope to gain.

Rep. Mike Gallagher
In the report, deterrence-by-denial becomes synonymous with the cybersecurity buzzword of “resilience” – the ability to keep functioning through an attack and restore normal operations rapidly afterward – but even this takes on a Cold War tinge. “I think one of the most unique and biggest parts of the report,” Rep. Gallagher said this afternoon, “is this concept of planning for continuity of the economy, in the way that, in the ’50s, we started planning for the unthinkable: how would we maintain continuity of government and continuity of operations in the event of a nuclear attack.”
What about deterrence by punishment? In the Cold War, that boiled down to a threat to massacre tens of millions of innocent civilians. Cyber weapons can’t physically do that, and if they could, it would hardly be a proportionate response to the theft of military secrets or even the sabotage of, say, a chemical plant that led to a deadly toxic spill. But that doesn’t mean the US cannot reliate for cyber attacks with cyber counter-attacks of its own.
“America’s commitment to international law appropriately places constraints on its willingness to implement deterrence by punishment in cyberspace,” the report says delicately. “In addition, scholars of cyber strategy debate the extent to which cyber capabilities offer a feasible punishment mechanism, or whether punishment requires lethal capabilities. Therefore, in cyberspace the preferred punishment strategy for democratic nations is to impose costs on adversaries through targeting key—often government or illicit, as opposed to commercial and civilian—networks and infrastructure used to conduct cyber campaigns.”
In other words, deter cyber attack by threatening to ravage any assets used to conduct such an attack.
The report also embraces Cyber Command’s controversial new strategy of “defending forward.” CYBERCOM’s concept effectively requires US hackers to maintain a watchful presence, not just in US systems, but on allied, neutral, and adversary networks so they can detect impending attacks and cut them off at the source. The Solarium Commission makes that approach a principle of its proposed national strategy.
“The strategy incorporates the concept of ‘defend forward” to reduce the frequency and severity of attacks in cyberspace that do not rise to a level that would warrant the full spectrum of retaliatory responses, including military responses,” the report says. “Though the concept originated in the Department of Defense, the Commission integrates defend forward into a national strategy for securing cyberspace using all the instruments of power.” (Traditionally, these instruments are known as the ‘DIME’: diplomatic, informational, military, & economic).
“Defend forward posits that to disrupt and defeat ongoing adversary campaigns, the United States must proactively observe, pursue, and counter adversaries’ operations and impose costs short of armed conflict,” the report continues. “This posture signals to adversaries that the U.S. government will respond to cyberattacks, even those below the level of armed conflict that do not cause physical destruction or death, with all the tools at its disposal and consistent with international law.
“This posture includes operating in ‘gray’ [neutral] and ‘red’ [adversary] space in a manner consistent with international law,” the report affirms.
SOURCE: Cyberspace Solarium Commission
In the commission’s layered defense strategy, the report goes on, “the cost imposition layer also demands that the U.S. government protect its ability to respond with military force at a time and place of its choosing, [because] a key, but not the only, element of cost imposition is the military instrument,” the report says. A whole chapter of the report goes into detail on ways to strength the US military. Many of them focus on better defending units, contractors, and weapon systems against cyber attack. But they include boosting offensive capabilities as well, particularly by growing CYBERCOM’s Cyber Mission Force.
“The CMF is currently considered at full operational capability, with 133 teams comprising a total of approximately 6,200 individuals,” the report acknowledges. “However, these requirements were defined in 2013,” it notes, long before the magnitude of threat to US elections and the economy became so painfully clear.
The Cyber Mission Force needs not only to grow larger, the report argues, but to move faster, which requires giving it new standing authorities to take action without time-consuming consultation – another controversial move.
“The pace of cyberspace operations may require delegated authorities and seamless decision making to pursue and deliver effects against adversary targets,” the report says. “Relevant authorities within the scope of Title 10 for conducting counter-cyber operations include not only authorities to deliver offensive cyber effects but also those that support planning and executing these operations.”
The italics in that sentence are ours – but the emphasis on the capacity to conduct cyber counter-offensives is clearly the commission’s.
Killer Apps: 5 stories highlight quiet progress on military AI and CJADC2
While combat has seen a drone revolution, the US has made subtle but real advances in applying AI to military planning, intelligence, and “all domain” command and control.