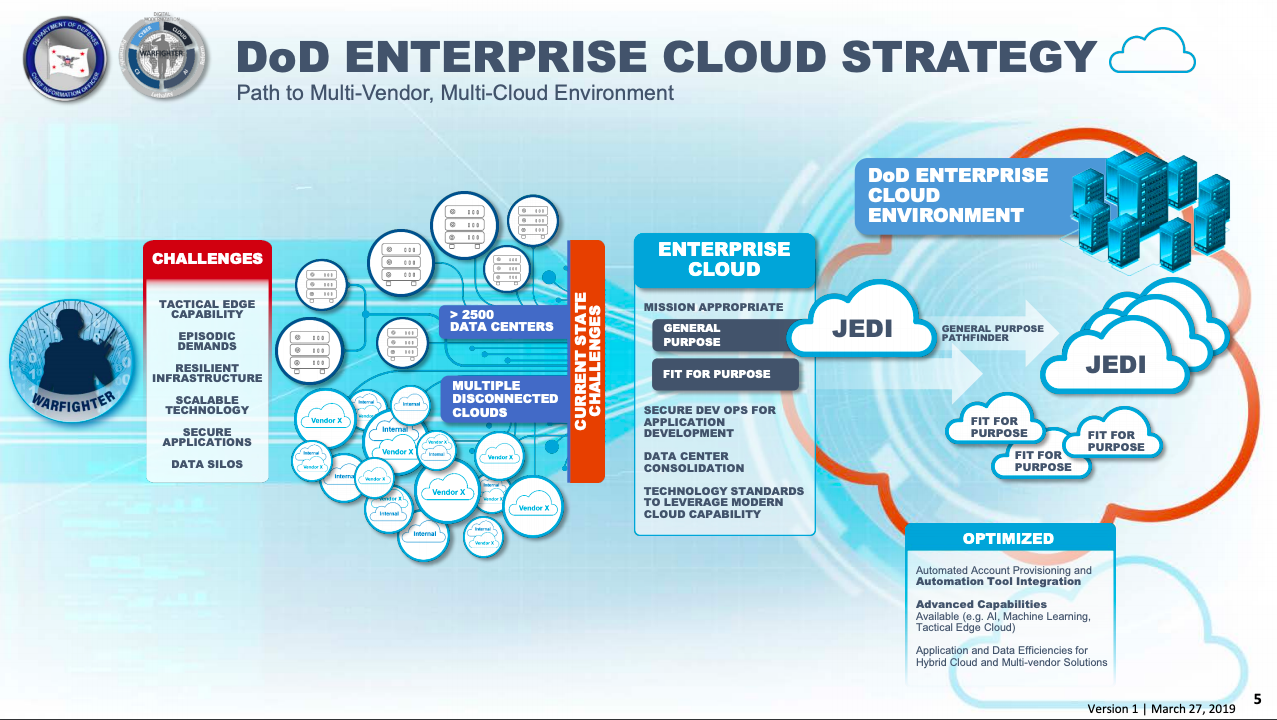
“We’re on the defense,” Ron Bushar, senior vice president at Mandiant says. “I don’t think we’ve hit a real deterrence level in this space yet. And that’s going to be key to thinking through our strategy over the next few years.”
By Colin Clark
Threat actors are targeting one newly discovered and three previously known vulnerabilities in Pulse Connect Secure enterprise VPNs, according to a CISA emergency directive and alert, as well as blog posts by FireEye and Ivanti. “There is no indication the identified backdoors were introduced through a supply chain compromise of the company’s network or software deployment process,” FireEye noted.
By Brad D. Williams
Security professionals are increasingly observing multiple threat actors, from nation-states to cryptominers, exploiting the vulnerabilities. As for China-based HAFNIUM, “This is part of the much larger Chinese effort to constantly be ferreting out new vulnerabilities and then exploiting them — with no end in sight,” said Heritage’s Dean Cheng. “The Chinese will pay close attention to the Biden administration response.”
By Brad D. Williams
CMMC 1 is “what you’ve got to have to make sure your neighbor is not in your Netflix,” quipped Stacy Bostjanick, director of CMMC. “It’s very easy, and commensurate with basic cyber hygiene. I recommend that everyone get there, but as a COTS provider, you don’t have to.”
By Kelsey Atherton
“This is the start of a new day in the Department of Defense where cybersecurity, as we’ve been saying for years is foundational for acquisitions, we’re putting our money where our mouth is. We mean it,” Katie Arrington says.
By Kelsey Atherton
The NSA cannot mandate patching on its own, but the new Cybersecurity Maturity Model Certification (CMMC) allows the Pentagon to penalize companies in its supply chain that fail to adequately protect their networks.
By Kelsey Atherton
Ellen Lord said DoD is working to develop a “microelectronics strategy,” to bring manufacturing and testing to the US
By Paul McLeary
Israeli officials said the message relayed during Secretary of State Mike Pompeo’s hours-long visit included a very specific political warning – Israel must stop any action that strengthens the Chinese Communist Party, even if that means canceling projects already planned.
By Arie Egozi
The head of the Pentagon’s Protecting Critical Technology Task Force wants to tighten security controls. That may conflict with the push to streamline acquisition.
By Sydney J. Freedberg Jr.
The Pentagon is struggling to speed up acquisition at the same time it’s imposing new cybersecurity controls. But one senior official has an idea for how to do both.
By Sydney J. Freedberg Jr.
“Security will be more important than speed in establishing a durable foundation for 5G’s future,” writes leading scholar Elsa Kania – and Washington must lead the way.
By Sydney J. Freedberg Jr.
“We didn’t bring one of these cases because of what’s going on on the trade front,” assistant attorney general John Demers said, “and we’re not going to drop them even if we reach an agreement.”
By Sydney J. Freedberg Jr.
Huawei founder Ren Zhengfei made a dramatic offer to let all comers license and modify his 5G technology. Making it secure would be a Herculean task.
By Sydney J. Freedberg Jr.
Vice Adm. David Kriete, deputy STRATCOM commander: “Strategic deterrence is active deterrence; it’s very dynamic.”
By Theresa Hitchens