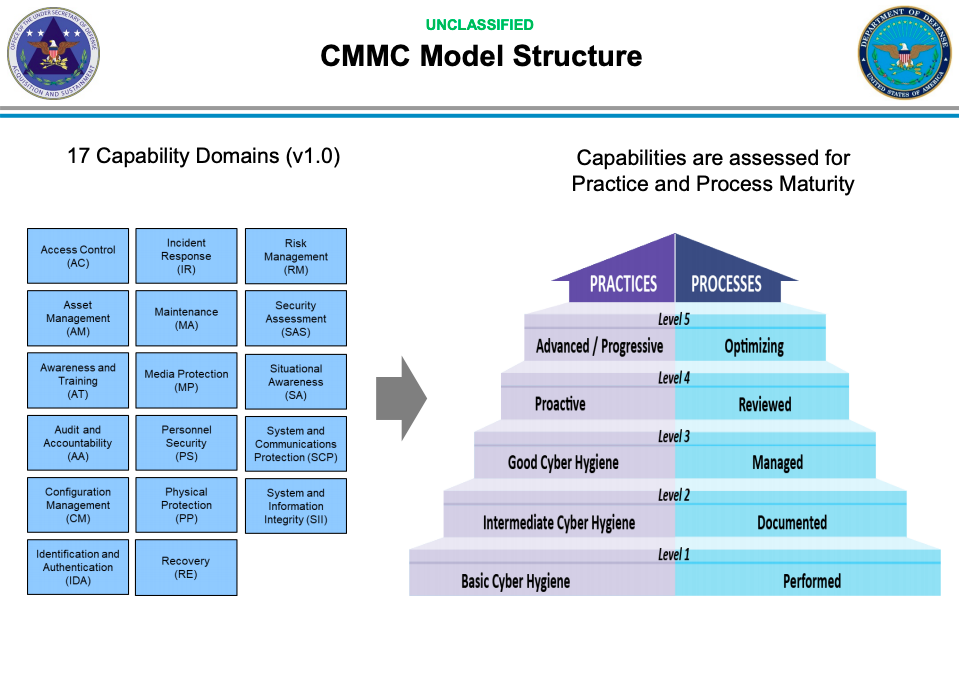
At its most basic level, under CMMC 2.0, defense contractors and subcontractors that have access to controlled unclassified information (CUI) will be required to demonstrate the “maturity” of their cybersecurity programs against a set of increasingly advanced capabilities.
By Jaspreet Gill
“In my mind, these are some of these avenues that we’re looking at at an idea phase now to see if we can put resources behind it,” said Robert Vietmeyer, director for cloud and software modernization.
By Jaspreet Gill
“I can tell you at DoD, we’re taking this very seriously,” DoD CIO John Sherman said. “And we are committed to implementing zero trust at scale for our four-million-person-plus enterprise that we lead.”
By Jaspreet Gill
“For instance, in the CMMC realm, rather than go out and assess each and every network of our industry partners, I’m kind of keen on establishing some sort of cloud services […]” said David McKeown, DoD deputy chief information officer and senior information security officer
By Jaspreet Gill
DoD said it will be “increas[ing] oversight of professional and ethical standards of third-party assessors.”
By Brad D. Williams
Designed to help secure the supply chain, CMMC requires the defense industrial base to protect Controlled Unclassified Information.
By Barry Rosenberg
“This is the start of a new day in the Department of Defense where cybersecurity, as we’ve been saying for years is foundational for acquisitions, we’re putting our money where our mouth is. We mean it,” Katie Arrington says.
By Kelsey Atherton
The alert “should raise concern for those simply focused on China or Russia as the core threat to our national security,” says Eric Noonan, CEO of security firm CyberSheath.
By Kelsey Atherton
NTIA is not aiming at eventual regulations; rather voluntary sharing of critical information about software supply chains.
By Theresa Hitchens
Undersecretary Ellen Lord took pains today to emphasize companies would have plenty of time and plenty of help to meet new security standards. Is she going too slow?
By Sydney J. Freedberg Jr.