
WASHINGTON: “You get whacked a lot.”
Those are the words of someone who should know, the leader of the aggressor squadron at Red Flag, the man who tries to kill U.S. forces. Lt. Col. Tyler Lewis, commander of the 57th Adversary Tactics Support Squadron at Nellis Air Force Base, echoed comments we’ve heard before, that he often had no idea he was going to die until he was declared dead. Why? The F-35’s combination of stealth, Electronic Warfare, cyber and sensors lets them find, target and destroy an enemy plane from beyond visual range.
For example, more fourth generation fighters died in one day than did F-35As during the entire exercise through Feb. 2. It began Jan. 23.
[read about the F-35A’s mission readiness at Red Flag]
(While working on this, I found a great quote by Capt. Stephanie Anne Fraioli that explains the fundamental difference between a fourth- and a fifth-generation aircraft: “With fourth-generation fighter airframes, speed and energy equaled life and survivability. In the fifth-generation realm, information equals life.”)
Most Red Flag coverage so far has focused on a statistic we’ve all heard. The F-35As at the Air Force’s toughest combat training exercises are killing enemy aircraft at a rate of 15-1. But one of the pilots flying the F-35s — Lt. Col. George Watkins, 34th Fighter Squadron commander — says: “The kill ratio isn’t that important. We are more focused on the SAM and IADS threat.” Think Russian-made S-300s and 400s.
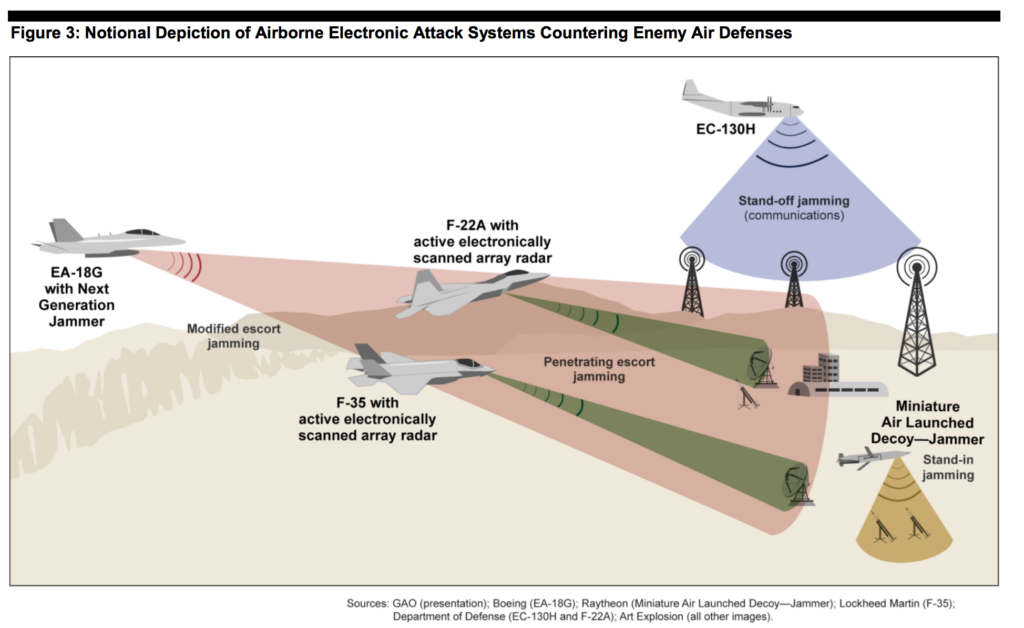
While older aircraft like the EA-18G and EC-130H jam enemy systems from a distance, stealthy F-22s and F-35s can conduct electronic warfare at close range. Note this depiction is from 2013, when F-35 concepts of operation were much less developed. (GAO graphic)
At this Red Flag, Watkins and Lewis said the Joint Strike Fighter faces the most dangerous IADS threats they’ve ever encountered at an exercise. The plane’s EW suite helps it find the threat, then they can use their stealth and jamming to “get in a lot closer to these threats than anyone else can,” Watkins told reporters. Then they can use their cyberwarfare capabilities, about which no one will talk on the record, and EW to neutralize the IADS. Or they can use a missile or bomb or a combination of all four.
I asked Lewis if his plane had been neutralized or affected by F-35 cyber attacks during this Red Flag. After a long pause, he chuckled and didn’t answer.
Also, the F-35s can gather the threat information and pass it to those less fortunate fourth-generation aircraft or, Watkins told us, “we can use stealth, jamming etcetera to get in a lot closer to these threats than anyone else can get.”
One of the little discussed of the F-35’s effectiveness is mission planning. Capt. Fraioli, whom I quote above, notes that mission planning plays a central role in making stealth (Low Observability to the professionals) effective during a combat mission. “Up until about six months ago mission planning was fairly difficult to do day to day because we have to decrypt everything,” Watkins said. Now they can change the data on a mission to mission basis. He also noted that the F-35As flying at Nellis had flown “126 missions without losing a single flight to maintenance” during this Red Flag.
On Tuesday we’ll be getting another shot at the F-35A pilots to discuss the exercises, which ended today.
Iran says it shot down Israel’s attack. Here’s what air defense systems it might have used.
Tehran has been increasingly public about its air defense capabilities, including showing off models of systems at a recent international defense expo.


























