 It’s conventional wisdom to declare that offense will always beat defense in cyberspace, because the Internet was designed with access in mind, not security. It’s a technological problem with strategic consequences as Russian and Chinese hackers rob us blind. But now DARPA, the agency that invented the Internet, is tried to reverse that situation by redesigning computer hardware and software from the ground up to make it more secure from hackers.
It’s conventional wisdom to declare that offense will always beat defense in cyberspace, because the Internet was designed with access in mind, not security. It’s a technological problem with strategic consequences as Russian and Chinese hackers rob us blind. But now DARPA, the agency that invented the Internet, is tried to reverse that situation by redesigning computer hardware and software from the ground up to make it more secure from hackers.
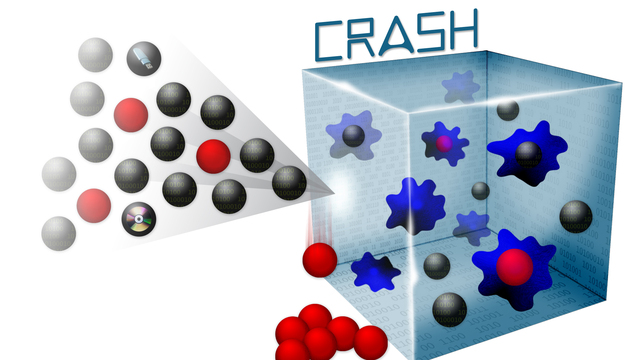
If the Defense Advanced Research Project Agency’s effort, called the CRASH program, succeeds, it could pave the way for new technologies that could make both government and private-sector computers not only more resistant to attack but also able to self-repair any damage that took place.
The goal of CRASH — a backronym for Clean-Slate Design of Resilient, Adaptive, Secure Hosts — is to develop new types of robust hardware and software that can better resist the ever-multiplying attacks and software exploits on both federal and commercial systems. These new systems would be very hard to penetrate and, even if compromised, would provide little useful information to a successful attack, CRASH program manager Howard Shrobe told Breaking Defense. “The fundamental goal is not perfection, but rather to make the cost-benefit trade-offs for attackers unattractive,” he said. “These systems should cost an attacker much more to successfully attack than the value gained by an attacker.”
CRASH is trying to redesign computers and software from the ground up to eliminate common design flaws used by attackers. Shrobe notes that almost all vulnerabilities are the result of a failure to enforce basic semantics, the rules that govern software language, in particular the inability to distinguish instructions from data, to recognize different types of data, and to restrict operations to those that make sense for specific data.
For example, current hardware allows operators to add a number and a “string” (a sequence of numbers, letters, special characters, and spaces), which can potentially allow hackers to damage or manipulate data at the hardware level. Systems today also are unable to consistently restrict information to only those authorized to see or modify data. The CRASH program is designing hardware that enforces all of these semantic constraints on every operation, Shrobe said.
The program is taking a multi-pronged approach to making computers and hardware more secure. It is a combined effort that looks at hardware, programming languages, operating systems, and theorems all at the same time. Under the program, hardware is designed to enforce basic semantics or operating rules. One way to do this is by tagging every individual piece of data with its type, size and ownership rights so that the system knows what it is and what it’s for.
At the software programming level, CRASH researchers are creating new languages that are explicit about information flow and access control rights. These languages allow programmers to state exactly what rules apply to each module of code, Shrobe said. The operating systems enforce these rules or “contracts” dynamically when the program runs. Statistical theorems can also be applied to verify that these contracts are being obeyed, he said.
CRASH is also changing things at the operating system level. Researchers are designing fundamentally new types of systems that are not built around a single software kernel that, if compromised, will give attackers complete control of a system. Instead, the program is designing operating systems made up of large numbers of cooperative but mutually independent modules, each designed with a specific purpose and the lowest level of access privileges needed to do that job.
The modules are also designed to be suspicious of each other, Shrobe said, checking one another’s results to make sure they obey their “contracts.” These structuring tools are not only available to the operating system, but equally to all system and application code. This creates a system where more than one component would have to be compromised for an attacker to succeed, he said: “Defense in depth is a core philosophy.”
Program researchers are also developing techniques that will potentially allow designers to make systems different from each other in the low level details–where a single small bug, found in many systems, can provide easy access to hackers–while allowing the systems to present uniform, easy-to-learn interfaces to their managers and users, Schrobe said.
Self-repair from attacks and tampering is another goal for CRASH. The program is looking into self-monitoring and self-adaptation technologies. Researchers are working at the hardware level to enforce basic operating rules, but also to extend checking and verification techniques up to and throughout the software systems as well.
When these self-monitoring systems detect a violation, they invoke built-in system services that attempt to diagnose the problem, using replay capabilities and reasoning techniques to isolate and characterize the problem; recover from the immediate problem by having multiple redundant methods to achieve any given goal; synthesize filters that can detect the same type of attack in the future and prevent it from succeeding; and automatically generate a patch to fix the underlying vulnerability.
It’s an ambitious technological challenge. But if it works, CRASH might change the balance of power in cyberspace between offense and defense.
Space Force celebrates 5th anniversary at growing Spacepower Conference
Our latest eBook offers updates on the Space Force and SPACECOM, showcasing the latest tech, and the challenges of modern space operations.